Who knows who’s calling you?!
What goes into figuring out an unknown phone number while maintaining privacy?

Living in India means dealing with spam calls everyday. I get at least 10 calls everyday out of which nine are spams and the tenth is a scam. Recently, regulators like Airtel have started identifying common spam/scam numbers and have started highlighting these numbers with a warning when the call is received. While this is a good first step, it is very limited and misses a huge set of numbers anyway.
A lot of Android users download Truecaller to deal with this problem. Truecaller is an app that stores a huge, active library of phone numbers which are categorised with the right names and are also classified as spam/scam based on user input. On Android, as soon as a phone call arrives, Truecaller runs that number against its database and is able to display a huge blue pop up (on some devices this is a full screen UI by Truecaller) that displays the caller ID and whether or not it is a spam call.
Now this is great, except that it is not for two reasons - one, the Truecaller interface is not very good-looking (and some of us really like aesthetics!) and two, more importantly, Truecaller just receives the number directly onto its servers and it stores that. The problem is that they also associate this number with you. So they know that you, the user, has received all these calls throughout the day. Although we don’t know how Truecaller uses this data, it is concerning to hand over all the call log information to a third party. It is also concerning that Truecaller was hacked in the past and hackers were able to get a lot of information about their users.
But what has the story been like on iOS?
iOS 13 to 17 - Live Caller ID, well, sorta!
When Truecaller launched on iOS, it was very primitive in functionality as Apple did not provide APIs for the app to read call logs. This meant that the app could find a number only if the user manually copied the number, opened the TrueCaller app and then pasted it. While this is also a useful feature to have, users preferred the live caller ID feature from Android where Truecaller would be able to proactively identify the caller without having to open the app.
Users wanted the same convenience on iOS as well. With iOS 13, Apple launched a feature that would allow apps like Truecaller to build a database of numbers on the client and that could be used to identify the callers.
Now, you might wonder what the advantage of doing this on-device was, because, Truecaller could still store this number when they were comparing it against their on-device database, right? Right?
Nope!
The way this feature worked was that developers had to create an iOS extension (if you are not familiar with the iOS programming landscape, an extension is like a mini-app that lives outside of the context of your app). And even then the extension could not compare the number by itself.
When a phone call occurred, iOS would ask the extension for its database and iOS would then compare the numbers by itself! So Truecaller never knew who was calling. The OS took the responsibility of comparing and showing the caller ID. All Truecaller could do was provide a list of numbers, caller IDs and warn whether it was spam or not - which Truecaller cleverly implemented with a checkmark or a cross before the name.
The OS would then display this name in the native calling UI - helping the user understand who was calling. This way, the aesthetics of the calling UI wasn’t altered in anyway either.
Well, this is great, right? Everybody wins and spam callers stay away.
Unfortunately, this was not the case because there are limits to what an on-device database can do. It’s also not easy to update a database like this and spammers are quick to use newer numbers to spam you.
So, even though the problem was partially solved, users still found the functionality lacking.
iOS 18 - Live Caller ID Lookup, this time for real!
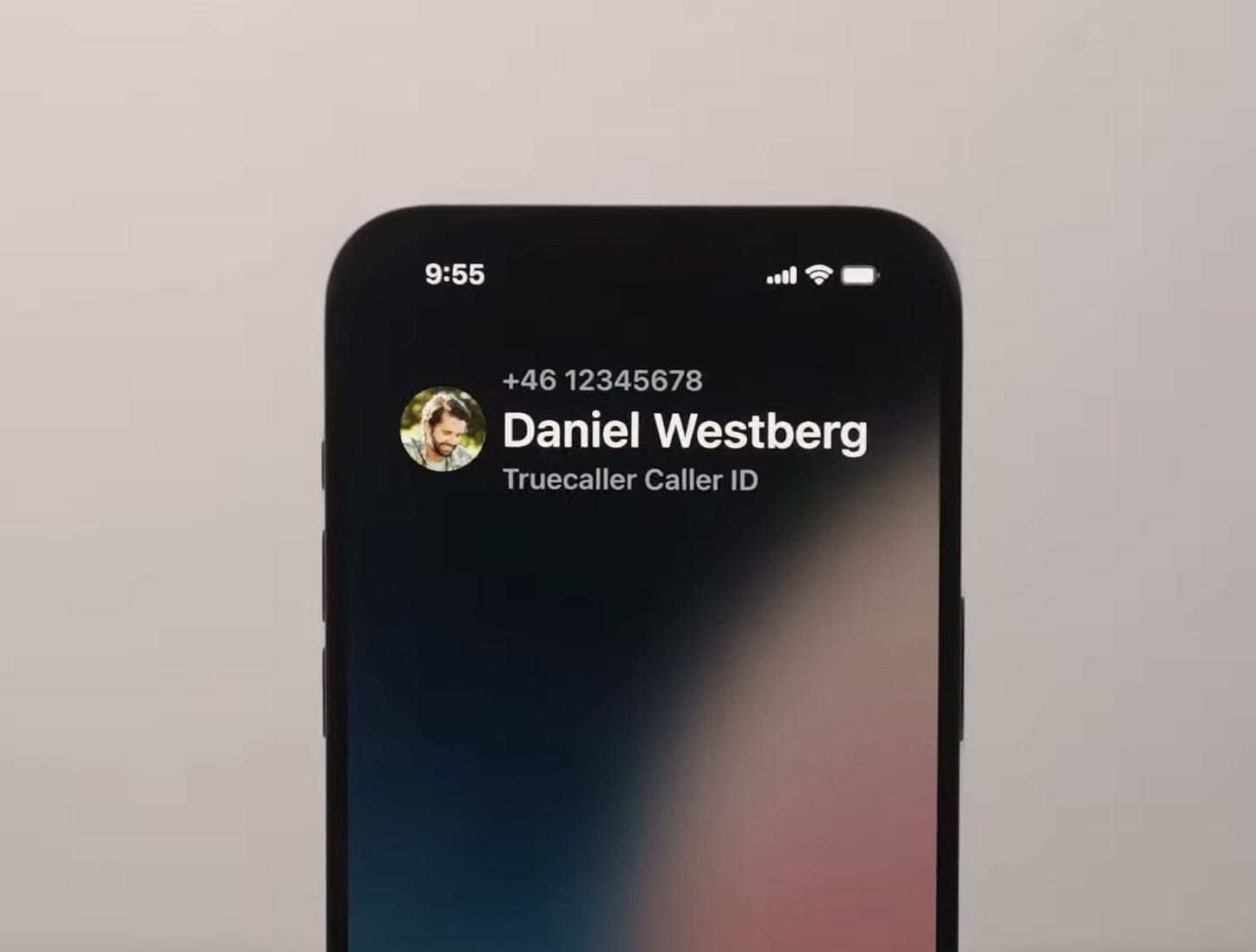
With iOS 18, Apple has finally implemented a mechanism where an app like Truecaller is able to query the number against it’s server full of numbers and figure out who is calling, all in real-time and display it back to the native calling UI.
But if the Truecaller server can query the calling number against its database, doesn’t this mean they can also store all our call logs like in Android?
Nope!
The amount of technical complexity that has gone into this is insane! It’s amazing that Apple’s engineers have dedicated time and effort to build for this use-case and it’s also amazing that the Truecaller team has taken the effort to build through these nuances and support this feature.
Behind the scenes, this whole mechanism is called KPIR - Keyword Private Information Retrieval. The idea behind this approach is that the keyword (the item to be searched in the database, aka, the currently calling phone number) can be matched against a database on the server and return a matching result, and all of this can be done without revealing to the server what the number is. This is enabled by a cryptographic concept called homomorphic encryption. Homomorphic encryption enables the server to perform computation on encrypted data without having to understand or decrypt the data.
That’s a lot of jargon so let’s try and break this down in the simplest way possible.
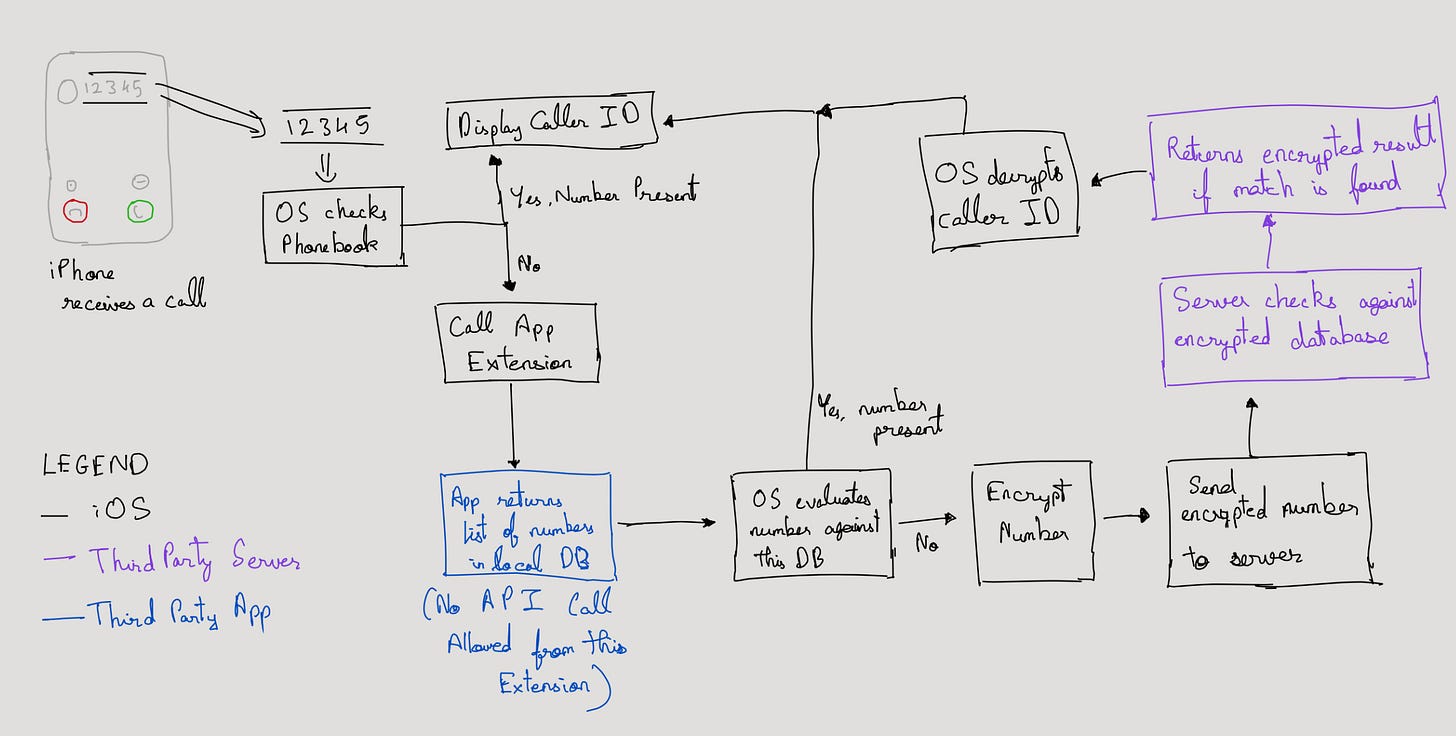
1. Truecaller has a huge database full of phone numbers that it’s constantly updating. Every time Truecaller gets a new version of this database, it creates an encrypted version of this database using a public key. This database is then hosted at a specific endpoint which can be queried by the Truecaller extension on iOS.
2. Once this table of numbers is encrypted by Truecaller on its server, even Truecaller cannot know which entry is which. Let’s say they had a list A -1, B-2, C-3 and so on, after encryption, it becomes xysdwe-we3r, sdsf23-2312, egdvl13-24r3cs .. (nerds - this is just a layman’s representation of encryption, don’t sue me 😂). Now Truecaller does not know which is A, B or C and it doesn’t have the private key to decrypt this data back into a sane form.
3. On the iOS side, when a phone number comes up, it is first encrypted in the same way the numbers on the database was encrypted. Again, Truecaller on iOS does not know what the number was before encryption.
4. After encryption, the number is sent to the server via an API call. The job of the server is to match this encrypted token with all the encrypted data on the database and return back an encrypted match. The server still has no clue what the returned data even means.
5. The device now receives this encrypted data which it is able to decrypt, thanks to a private key it has. Again, the decrypted data is also not shown to the Truecaller app, only to iOS.
6. iOS now successfully depicts the caller ID against the phone number in the same native calling UI we all know.
There’s a lot of effort involved here from Truecaller because every time a new number gets added to their database, they need to create a whole new version of their encrypted database just for their iOS users. So essentially, they are maintaining two different databases - one for Android and one for iOS. They will have to ensure the data on both are the same every time.
But this mechanism is fantastic because iOS ensures that no third party app ever gets to know who’s calling you while you still get all the benefits of Truecaller, similar to Android!
I have also observed (and honestly, this simply makes sense), the order in which the OS seems to gauge numbers is -
1. First check if the phone number exists in the contact book, if yes, then display the caller ID. If no, go to step 2
2. Check if it exists with one of the offline databases - yes, the older version of matching still exists. If yes, display the caller ID. If no, go to step 3
3. Check if it exists with the server’s database over API. If yes, display the caller ID. If no, then all options are exhausted, just show the number.
Okay, so why is Truecaller trying so hard?
If you read all of that and wondered, wait, why is Truecaller doing so much hard work and putting up with all the hoops Apple is putting its way, I wouldn’t blame you. That’s a lot of technical work to support just the iOS platform. I am sure you would also find it more puzzling when you learn that out of Truecaller’s 435 million users, only 7% are iOS users.
But at the end of the day, more than the number of users, it’s the revenue that matters to any business. And even though the iOS user base is just 7%, they create more than 40% of the revenue for Truecaller. That’s a significant amount and it’s only going to increase as Truecaller becomes a better first-class iOS citizen with features like this. After learning about the engineering that goes behind this, I have installed Truecaller on my phone, knowing that my data is safe. I am sure a lot of others would do so too in the coming months.
More than anything, this API is a great example to show that Apple is willing to open up their ecosystem to add features that users want without compromising their privacy. This is the best of both worlds. I can’t wait to see what the future holds and I am excited for all the new things Apple will release with iOS 19.
If you liked this essay, also check out my last post about hidden UX complexities and how people get affected by it -